Contact us today: (888) 973-3737 | info@cnp.net
Cybersecurity Resources
Learn about business data security and more
Featured

Cybersecurity in 2022
Learn all about cybersecurity in 2022 including a checklist of the 25 best cybersecurity practices, 4 steps to patch management, the importance of cyber insurance, and how to secure your business now and in the future.
Recommended Resources
Product Info
Case Studies
Videos
eBooks
Infographics
Reports

CNP Technologies Brochure 2022
CNP Technologies has been delivering unified communications, data and network infrastructure, and security to companies across the United States from our headquarters in Charlotte, NC for over 22 years.

Making Cybersecurity Mesh Architectures a Reality
Learn how a cybersecurity mesh architecture (CSMA) can unify your fragmented infrastructure and deployments, create cohesion, and enable collaboration and automation across your entire environment.

Removing the Complexity of Your Risk and Compliance Journey
With Foresite’s Integrated Risk Management (FIRM) Platform, you can simplify and automate much of the compliance process and remove the complexity of your risk and compliance journey. Find out how:

Secure Unified Communications from FortiVoice Cloud
With FortiVoice Cloud your team can call, conference, chat, and even fax through an all-inclusive and, most importantly, a secure unified communications solution.

Foresite – Managed IT Security Services
CNP Technologies introduces Foresite, a global service provider delivering a range of managed security services designed to help our clients meet their information security and compliance objectives.

Fortinet CTAP OneSheet
When was the last time you performed a vulnerability assessment on your network that did not require a vendor to spend hours on site? Discover a quick and easy way to test your next-generation firewall technology without disrupting your network.

Local Government Cyber Threat Detection
The City’s IT services must be available 24/7, but the internal IT staff is only available from 8 am – 5 pm, Monday through Friday, leaving significant gaps of time where cyber exploits could go undetected. Find out how Foresite helped.

Finance Security Assessment
A financial services firm had regulatory audits coming up. Foresite’s IT Security resource consulted with the firm’s stakeholders to confirm their objectives for this project.
Cloud Security 101
Secure Unified Communications from FortiVoice Cloud
Preventing Cyberattacks:
7 Ways to Keep Your Company Safe

Best Practices for API Security
Centralized and consistent security controls are often not yet in place, and 62% of businesses have delayed app rollouts because of API security concerns. In this eBook, Fortinet will examine the best techniques to defend your APIs against security threats:

Cybersecurity in 2022
Learn all about cybersecurity in 2022 including a checklist of the 25 best cybersecurity practices, 4 steps to patch management, the importance of cyber insurance, and how to secure your business now and in the future.

5 Ways Software Assurance Helps Your Business Succeed
Mitel Software Assurance provides access to upgrades, incremental enhancements, fixes, security patches, and expert technical support. Learn 5 ways SWA helps your business succeed:

The Ultimate Guide to VMware Data Backup
Make sure you have the best recovery methods and data protection strategies in place. Learn five tips for better virtual machine backup and more in this VMware Backup for Dummies eBook:

Secure Your Small Business Office
This guide to creating an awesome and secure IT experience for your small business will help you learn how to manage issues such as WFH data security, social distancing in hybrid offices, cybersecurity, and more!

25 Best Practices for Basic Cybersecurity
This checklist of 25 best practices for basic cybersecurity will help you prioritize where you should put your focus when it comes to cyberthreat protection in 2022 and beyond.

Make Hackers’ Jobs Harder, Not Yours
Today’s users need a network that allows them to connect to any resource from any location using any device. Learn how you can protect every edge, make hackers’ jobs harder, and make your easier:
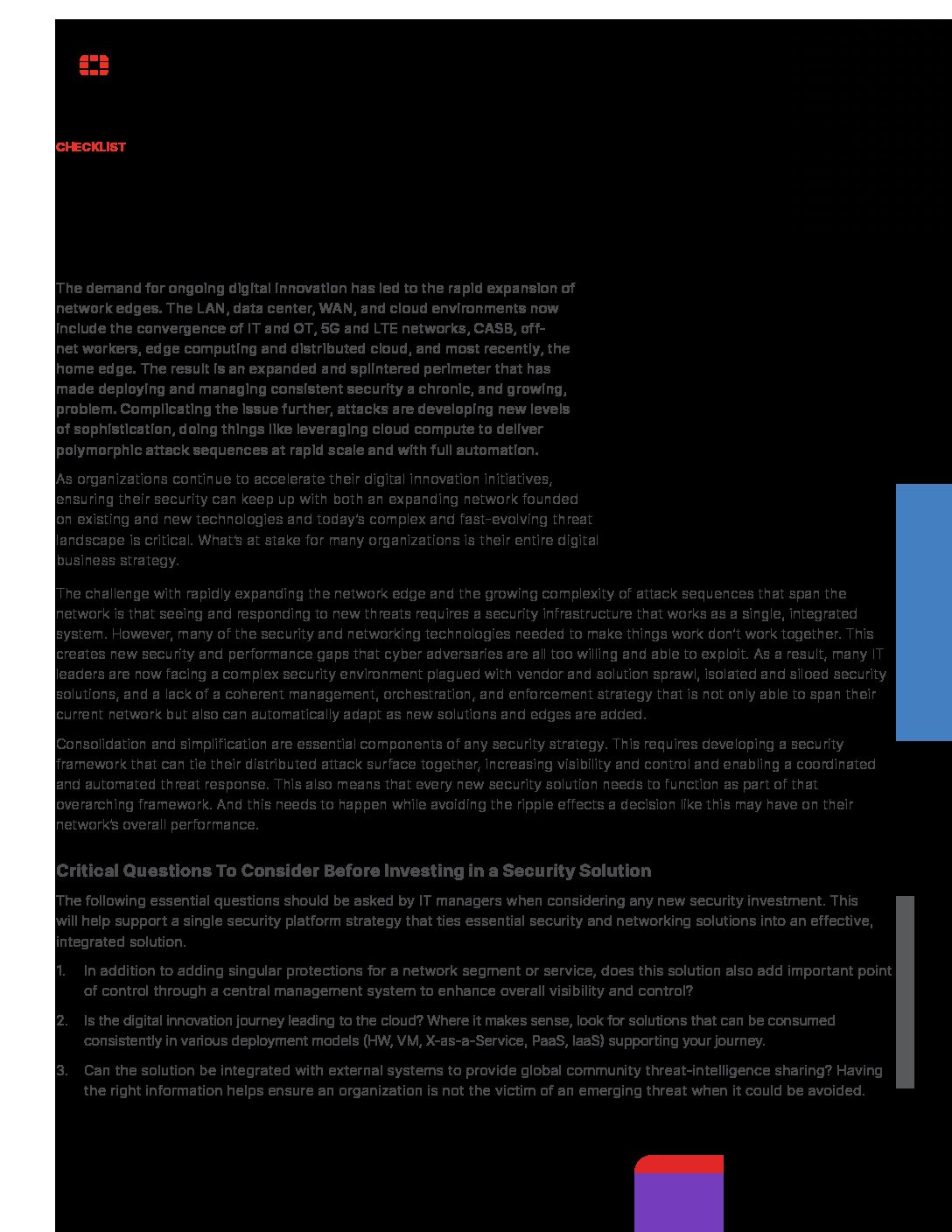
10 Key Questions to Consider Before Making a Security Investment
Supporting your security strategy with the right features, solutions, and vendor is integral in todays business environment. Use this checklist to cover your bases:

Checklist – What to do in the Midst of a Ransomware Attack
If you’ve not yet been a victim of ransomware, the odds are, it’s only a matter of time. Here’s a quick checklist of the steps your business should take to deal with an active ransomware attack:

The Present and Future of Cloud SASE
Secure Access Service Edge (SASE) represents the future of secure connectivity. However, with a sprawling set of capabilities, it’s difficult to know what to prioritize.

7 Top Email Security Terms You Should Know
This short glossary will help you and your team recognize the most important email security definitions. Add it to your arsenal so you can keep your company’s data and information safe:
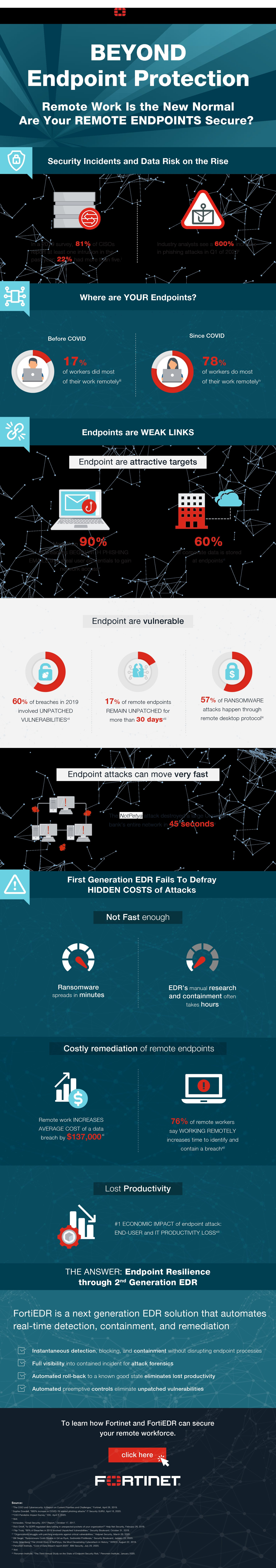
BEYOND Endpoint Protection with Fortinet
Remote work is the new normal, but are your remote endpoints secure? With security incidents and data risks on the rise, it's important to make sure!
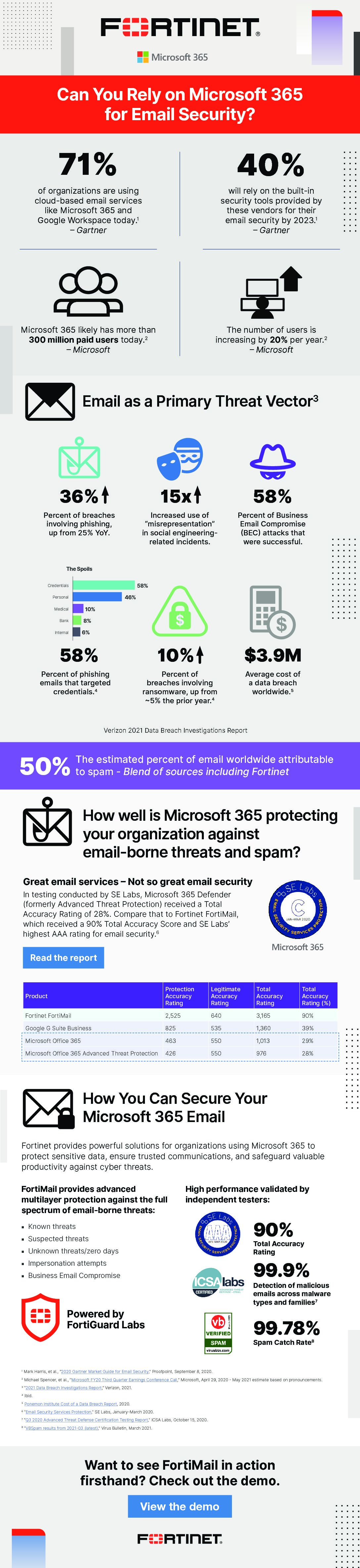
Can You Rely on Microsoft 365 for Email Security?
Email is today's primary threat vector, and this includes for business. With 71% of organizations today using cloud-based email services such as Microsoft 365, it's important to make sure you're secure!
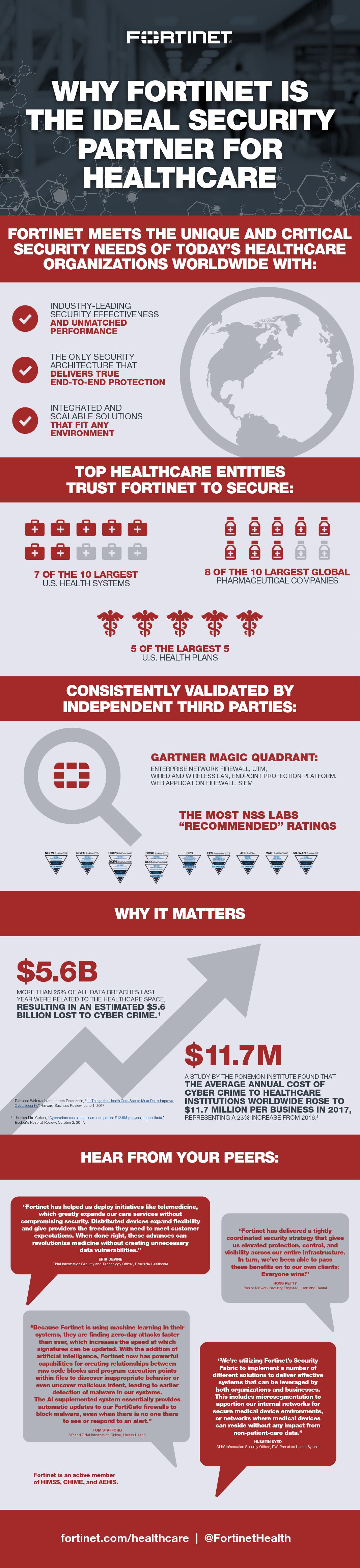
Why Fortinet is the Ideal Security Partner for Healthcare
Learn how leveraging Fortinet’s security solutions can help you to implement and deliver effective systems that can be trusted by your healthcare organization.

Challenges of the Cybersecurity Skills Gap
Check out this report to learn why cybersecurity professionals are imperative to business success and steps you can take in your organization to fill the gap:

The State of Phish
Learn about the impact of phishing plus how to inform and build your cyber defense, create user awareness, identify gaps in your security, and more in this state of phishing report from Proofpoint.

Cyberthreat Predictions for 2022: An Annual Perspective
Implementing security strategies to detect and intervene when something unexpected happens is harder than it sounds. This whitepaper from FortiGuard Labs explains the threat landscape for 2022 and offers some advice on how to prepare.
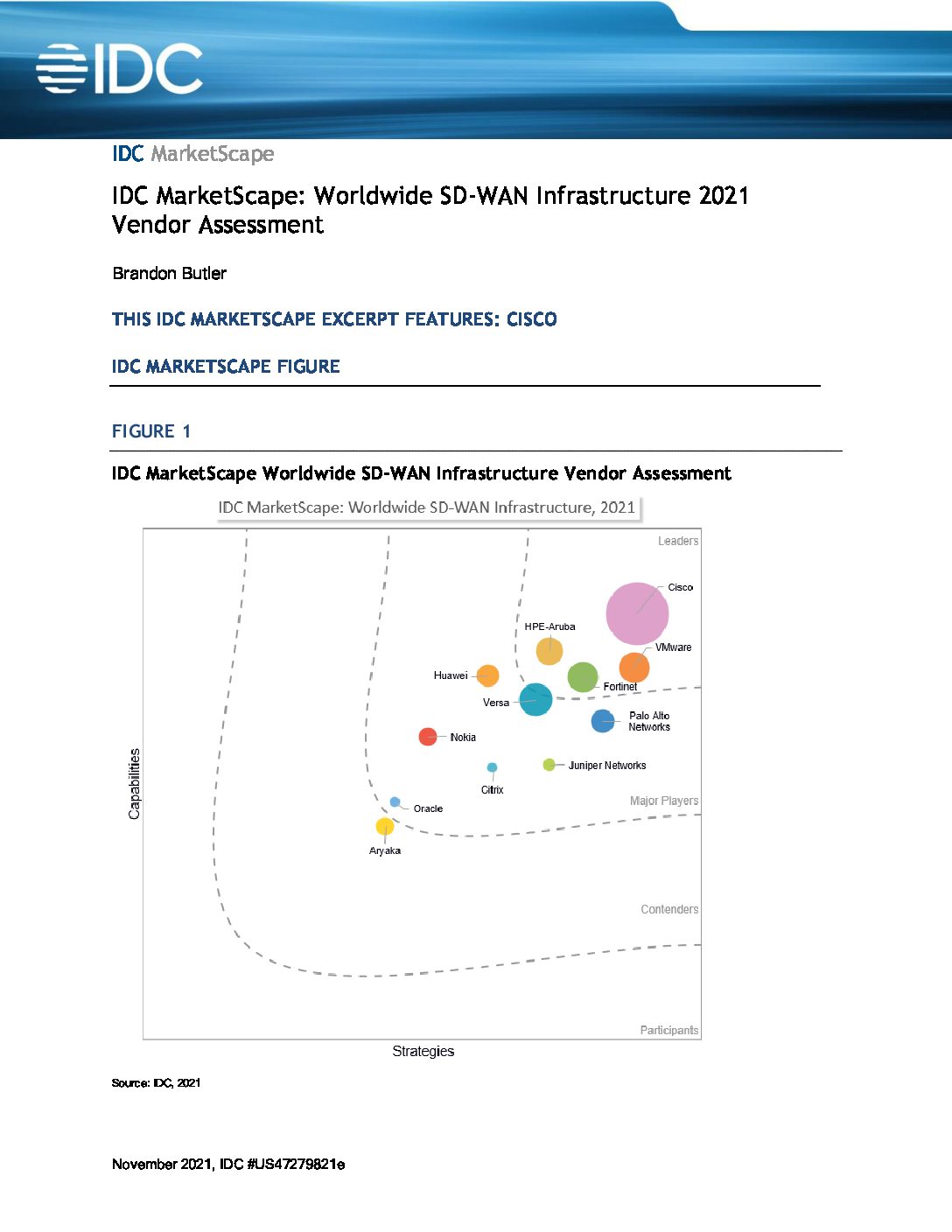
Cisco SD-WAN leads in IDC MarketScape 2021
Providing the connectivity, security, and automation required to simplify networks is imperative, which is why we’re excited to announce that Cisco SD-WAN has been named a Leader in the IDC MarketScape: Worldwide SD-WAN Infrastructure 2021 Vendor Assessment! Check it out:

Current Cybersecurity Priorities and Challenges for the CISO
These days, the CISO role can potentially make or break a business. This CISO and Cybersecurity Report from Fortinet takes a snapshot of how CISOs are approaching cybersecurity and the challenges they're currently facing:

Digital Security, Everywhere You Need It
If recent headlines are any indication, cybersecurity isn’t getting the priority it deserves in modern business strategy. Significant progress is needed in order to effectively thwart cyberattacks. Learn how Fortinet is combating this culture through cutting-edge technology and how you can get the digital security you need, everywhere you need it:

Ransomware, the Exploding Cyber Threat
In this whitepaper, Fortiguard Labs shares information from their global data analysis on the trajectory and impact of ransomware. You’ll also gain a more thorough understanding of what ransomware is, how it works, who it targets, and how you can protect yourself.

Contact Center Disaster Recovery and Business Continuity
Disaster recovery and business continuity plans to prepare for unexpected events have become must-haves for most companies. However, if you operate a contact center, it doesn’t take a much to have a disastrous impact on your business.

Email Risk Assessment Report
Check out these key findings from this email risk assessment from Fortinet and CNP Technologies so you can mitigate email borne threats and optimize your overall email experience.

Securing Hybrid and Multi-Cloud Environments
Cloud computing has transformed how we consume and deploy IT solutions. This whitepaper explores how you can develop your solution checklist for the changing paradigm.

How SMBs Can Secure Endpoints and Remote Workers for the Long-haul
Having a large number of remote users operating outside the corporate network changes cybersecurity priorities and increases risk. Learn the 4 parts of a successful security solution in this "new normal."

Top 7 Cybersecurity Threats and Challenges
As pharmaceutical companies increasingly digitize data and store it online, they become more susceptible to pharmaceutical cyberattacks. Learn the top 7 threats you should be looking out for, and how to mitigate them, in this whitepaper from Fortinet.

Protecting IT & OT Resources Against Advanced Security Threats
Manufacturing organizations manage expensive and sophisticated equipment at their factories—and the systems that run the machinery are increasingly being connected to the internet. The cybersecurity implications of this trend are significant.